- Beranda
- Komunitas
- Tech
- Crypto World Indonesia
What is hash? Outstanding features of hash function
TS
davidma.azcoin
What is hash? Outstanding features of hash function
Hash is a function that converts input data into a fixed-size string of characters. It serves as a cornerstone in cybersecurity, ensuring data integrity and security.

Hash in cryptocurrency is a mathematical process used to transform input data into a fixed-length string of values called a hash. This process utilizes hash functions like SHA-256, Scrypt, Ethash, Blake2, X11 to calculate and generate hash values from data such as transaction information or data blocks on the blockchain.
Outstanding features of hash function
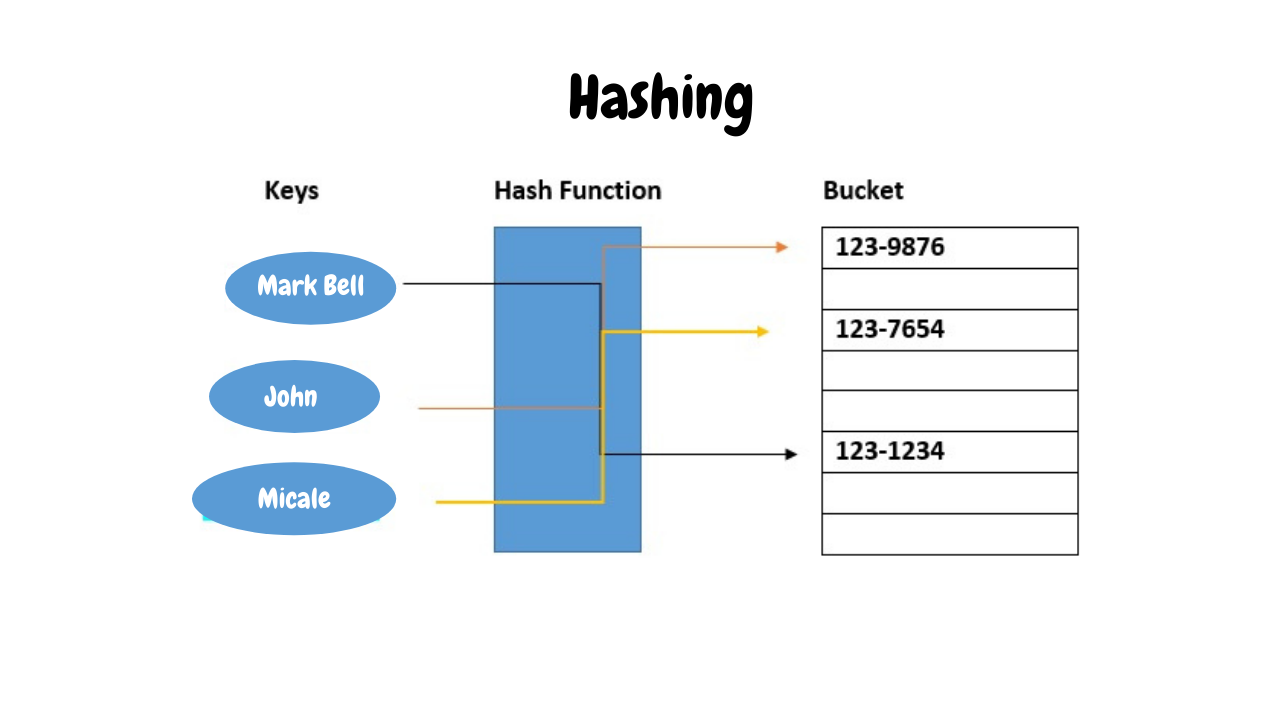
Hash in cryptocurrency has several important characteristics:
🐬 Uniqueness: A unique input data will produce a unique hash value. Even a minor change in the input data will result in a completely different hash value.
🐬 Non-reversibility: It's impossible to deduce the original input data from the hash value. This means you cannot determine specific information about the input data based solely on the hash value without the original input data.
🐬 Security: The hash value is unique to each input data and can't easily be reversed to determine the original data. This makes hash functions crucial for security and verification of transactions on the blockchain.
In summary, hash functions in cryptocurrency play a critical role in ensuring data integrity, security, and the decentralized consensus process through mining.
You can see more at:
🌵 https://kuula.co/explore/collection/7KYcJ/
🌵 https://devpost.com/software/what-is-market-cap-how-to-calculate-market-cap-in-crypto
🌵 https://davidma1980.pixnet.net/blog/post/153374368
🌵 https://www.artstation.com/artwork/04yPE5
Advantages and disadvantages of hash
Advantages
🔥 High security: Hashing helps securely protect personal information and transactions on the blockchain network due to the unpredictable nature of hash values.
🔥 Data integrity: Hash ensures that data remains unchanged during transmission or storage, thereby enhancing the system's integrity.
🔥 High performance: Using hash optimizes the verification and processing of transactions on the blockchain network, enhancing system efficiency.
🔥 Easy verification: Hashing simplifies transaction verification, reducing the risk of fraud and manipulation.
🔥 Resource efficiency: Hash usage minimizes system load and conserves computer resources.
Disadvantage
☔ Hash collision: This is a situation where two different pieces of data produce the same hash value, leading to potential information falsification. However, the probability of hash collisions is very low.
☔ One-way nature of hash: Despite being a one-way process, it's impossible to recover the original data from the hash value, which can pose challenges in cases requiring access to the original data.
☔ Computational cost: Computing hashes sometimes demands significant computer resources and time, especially for complex hash functions.
☔ Predictability: Although hashes aren’t predictable, in some cases, hackers can use brute force techniques to predict hash values.
☔ Algorithm dependency: The performance and security of hashing depend on the specific algorithm used, and if the algorithm is compromised, it can pose risks to the system.
Popular types of hash
Currently, there are numerous hash functions used in cryptocurrency and blockchain projects. Here are some of the most common hash functions:
🛬 SHA-256: SHA-1 (Secure Hash Algorithm 1) is a type of hash designed to replace MD5. It produces a 160-bit hash value and is widely used in security applications such as data encryption and authentication.
🛬 SHA-256: SHA-256 and SHA-512 are improved versions of SHA-1, generating hash values of 256 bits and 512 bits respectively. Due to their longer length, they are considered more secure and less vulnerable to attacks compared to SHA-1. They are widely used in modern security applications such as blockchain, digital signatures, and data authentication.
🛬 Scrypt: Scrypt is used in various cryptocurrencies like Dogecoin, Litecoin, and Dash. Its notable feature is its use of large amounts of memory and computation to generate hash values, thereby making mining more challenging.
🛬 Ethash: Ethash is used in Ethereum and ERC-20 based cryptocurrencies. Its distinctive feature is its requirement to simultaneously compute transactions and hashes, making mining more complex.
🛬 Blake2: Blake2 hash function is an improved version of Blake and is used in cryptocurrencies like SiaCoin. Blake2 offers fast processing speeds and high efficiency, enhancing transaction verification.
🛬 X11: X11 is a sequence of 11 different hashing functions used in Dash coin mining. Utilizing multiple hashing functions enhances security and complicates the mining process.
These hash functions play critical roles in ensuring the security and efficiency of various blockchain operations and cryptocurrency transactions.
Conclusion
Hopefully the information about hashes and the outstanding features of the hash function have helped you better understand their important role in data security and information authentication. For more details and how to apply them in practice, follow AZcoin's articles
Explore the remarkable features of hash functions and follow AZ coin detailed insights into their pivotal role in modern digital security.
What is hash?

Hash in cryptocurrency is a mathematical process used to transform input data into a fixed-length string of values called a hash. This process utilizes hash functions like SHA-256, Scrypt, Ethash, Blake2, X11 to calculate and generate hash values from data such as transaction information or data blocks on the blockchain.
Outstanding features of hash function

Hash in cryptocurrency has several important characteristics:
🐬 Uniqueness: A unique input data will produce a unique hash value. Even a minor change in the input data will result in a completely different hash value.
🐬 Non-reversibility: It's impossible to deduce the original input data from the hash value. This means you cannot determine specific information about the input data based solely on the hash value without the original input data.
🐬 Security: The hash value is unique to each input data and can't easily be reversed to determine the original data. This makes hash functions crucial for security and verification of transactions on the blockchain.
In summary, hash functions in cryptocurrency play a critical role in ensuring data integrity, security, and the decentralized consensus process through mining.
You can see more at:
🌵 https://kuula.co/explore/collection/7KYcJ/
🌵 https://devpost.com/software/what-is-market-cap-how-to-calculate-market-cap-in-crypto
🌵 https://davidma1980.pixnet.net/blog/post/153374368
🌵 https://www.artstation.com/artwork/04yPE5
Advantages and disadvantages of hash

Advantages
🔥 High security: Hashing helps securely protect personal information and transactions on the blockchain network due to the unpredictable nature of hash values.
🔥 Data integrity: Hash ensures that data remains unchanged during transmission or storage, thereby enhancing the system's integrity.
🔥 High performance: Using hash optimizes the verification and processing of transactions on the blockchain network, enhancing system efficiency.
🔥 Easy verification: Hashing simplifies transaction verification, reducing the risk of fraud and manipulation.
🔥 Resource efficiency: Hash usage minimizes system load and conserves computer resources.
Disadvantage
☔ Hash collision: This is a situation where two different pieces of data produce the same hash value, leading to potential information falsification. However, the probability of hash collisions is very low.
☔ One-way nature of hash: Despite being a one-way process, it's impossible to recover the original data from the hash value, which can pose challenges in cases requiring access to the original data.
☔ Computational cost: Computing hashes sometimes demands significant computer resources and time, especially for complex hash functions.
☔ Predictability: Although hashes aren’t predictable, in some cases, hackers can use brute force techniques to predict hash values.
☔ Algorithm dependency: The performance and security of hashing depend on the specific algorithm used, and if the algorithm is compromised, it can pose risks to the system.
Popular types of hash
Currently, there are numerous hash functions used in cryptocurrency and blockchain projects. Here are some of the most common hash functions:
🛬 SHA-256: SHA-1 (Secure Hash Algorithm 1) is a type of hash designed to replace MD5. It produces a 160-bit hash value and is widely used in security applications such as data encryption and authentication.
🛬 SHA-256: SHA-256 and SHA-512 are improved versions of SHA-1, generating hash values of 256 bits and 512 bits respectively. Due to their longer length, they are considered more secure and less vulnerable to attacks compared to SHA-1. They are widely used in modern security applications such as blockchain, digital signatures, and data authentication.
🛬 Scrypt: Scrypt is used in various cryptocurrencies like Dogecoin, Litecoin, and Dash. Its notable feature is its use of large amounts of memory and computation to generate hash values, thereby making mining more challenging.
🛬 Ethash: Ethash is used in Ethereum and ERC-20 based cryptocurrencies. Its distinctive feature is its requirement to simultaneously compute transactions and hashes, making mining more complex.
🛬 Blake2: Blake2 hash function is an improved version of Blake and is used in cryptocurrencies like SiaCoin. Blake2 offers fast processing speeds and high efficiency, enhancing transaction verification.
🛬 X11: X11 is a sequence of 11 different hashing functions used in Dash coin mining. Utilizing multiple hashing functions enhances security and complicates the mining process.
These hash functions play critical roles in ensuring the security and efficiency of various blockchain operations and cryptocurrency transactions.
Conclusion
Hopefully the information about hashes and the outstanding features of the hash function have helped you better understand their important role in data security and information authentication. For more details and how to apply them in practice, follow AZcoin's articles
0
24
0
Komentar yang asik ya
Komentar yang asik ya
Komunitas Pilihan