- Beranda
- Komunitas
- Entertainment
- The Lounge
Informasi VirusRansomware Cryptolocker,Cryptorbit/Howdecrypt,Bitcrypt & CryptoDefense
TS
Comdark.Bubnix
Informasi VirusRansomware Cryptolocker,Cryptorbit/Howdecrypt,Bitcrypt & CryptoDefense
Informasi Tentang Virus Ransomware Sejak tahun 2014 hingga tahun 2016



Selamat datang agan dan sista di trit ane yang agak rumit ini


 dulu yak
dulu yakJangan bilang
 ,karena ane sengaja bikin dimari agar agan dan sista bisa terhindar dari virus ini, dan juga ane udah pasang info ini di SF Computer sejak tgl 14 Januari 2014.
,karena ane sengaja bikin dimari agar agan dan sista bisa terhindar dari virus ini, dan juga ane udah pasang info ini di SF Computer sejak tgl 14 Januari 2014.Nah Di sini ane mau menyampaikan informasi tentang virus jenis baru yaitu virus tipe Ransomware.
jaman sekarang,tren virus udah beralih,tidak lagi menyerang system tetapi menyerang data dengan cara data dienkripsi lalu dijadikan sandera agar virus maker bisa minta duit tebusan.
virus jadul macam sality, virut, cuman menghancurkan sistem doank/exe. kompi di format/di install ulang,dah beres,ilang tuh virus,data pun tetep aman.
tetapi virus jenis baru ransomware,tidak menyerang sistem tetapi menyerang data dengan cara data dienkripsi untuk dijadikan sandera. Jadi otomatis,meskipun kompi mau di instal ulang ribuan kali,data tetap akan terencrypt. Untuk membuka enkripsi hanya bisa melalui proses dekripsi.
So, sangat disarankan jangan install ulang,karena di beberapa ransomware, ada kemungkinan private key yang ditinggalkan virus tsb yang berguna untuk membuka data kita/untuk proses Decrypt.
jangan heran jga kalo beberapa kali virus ini ahli lolos dari penjagaan antivirus yang terbaik/berbayar sekalipun,karena mereka memang tidak merusak sistem,cuman merusak data kita.
Oke, langsung aja cekidot penjelasan dibawah ini

VIRUS RANSOMWARETERBARU 2016
A. TeslaCrypt atau AlphaCrypt ( Februari 2015 Hingga RESMI BERHENTI BEROPERASI 19 MEI 2016 DAN MERILIS MASTER DECRYPTION KEY)

BERITA GEMBIRA !!!! TESLACRYPT RANSOMWARE RESMI BERHENTI BEROPERASI DAN MERILIS MASTER DECRYPTION KEY. ARTINYA SMUA JENIS TESLACRYPT BAKAL BISA DIDECRYPT SECARA GRATIS. CARA DECRYPTNYA BUKA LINK INI : http://www.bleepingcomputer.com/news...ecryption-key/SEBARKAN GAN.
A. INFO TERKINI :
Teslacrypt ini lahir nya aslinya akhir Februari 2015,tapi terus meraih kepopuleran hingga puncaknya di tahun 2016 ini.
Ketika pc agan kena virus teslacrypt ini,maka data agan akan terenkripsi menggunakan AES enkripsi,sehingga data agan gak akan bisa dibuka lagi,dan hanya bisa dibuka pake decrypt.
Virus Teslacrypt ini, karena exist sejak 2015 hingga sekarang 2016, punya banyak banget ciri khas,seperti ransom notes yg berbeda2 namanya dan ekstensi tambahan yg juga berbeda2 hingga versi teslacrypt pun berganti2 dari 1.0 lalu 2.2.0 hingga skrg di 2016 ini sudah versi 3.0.
Well,silahkan disimak beberapa penjelasan teslacrypt yg ane pajang di bawah ini

Info lengkap tentang teslacrypt mulai dari ciri2 nya, sampai decryptor, silahkan menuju ke post nomer 2 atau silahkan klik link berikut ini : http://www.kaskus.co.id/show_post/53...0b528b487c/2/-
B. Cerber Ransomware (26 Februari 2016 )

Di Indonesia,virus cerber ini mulai beraksi pertama kali pada tanggal 26 Februari 2016 berdasarkan laporan agan God-fatheR di sini http://www.kaskus.co.id/show_post/56...8b456a/2647/-.
virus cerber ini termasuk ransomware yang baru dan berasal dari rusia. Uniknya lagi virus cerber ini bisa ngomong loh !!
Cerber ini menggunakan mekanisme AES untuk mengenkrip file korban. uang tebusannya sekitar 1.24 bitcoin. namun sayangnya belum ada cara untuk decrypt cerber ini.
bagi para korban cerber,bisa mengunjungi web ini untuk mendapat info yg lebih lengkap : CERBER Ransomware Support and Help Topic.
A. Proses Enkripsi Cerber
When first run, Cerber will check to see if the victim is from a particular country. If the computer appears to be from any of the following countries, it will terminate itself and not encrypt the computer.
Code:
Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, Uzbekistan
If the victim is not from one of the above countries, Cerber will install itself in the %AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\folder and name itself after a random Windows executable. For example, when we performed our analysis of the ransomware it named itself autochk.exe. It will then configure Windows to automatically boot into Safe Mode with Networking on the next reboot using the following command:
Code:
C:\Windows\System32\bcdedit.exe" /set {current} safeboot networkCerber will then configure itself itself to start automatically when you login to windows, execute as your screensaver when your computer is idle, and set a task to execute itself once every minute. In this phase, when the ransomware is executed it will show a fake system alert and begin a restart process. Until this restart is allowed to occur, it will continue to display fake system alerts. Examples of alerts you may see include:
For some unknown reason, the computer will then reboot into Safe Mode with Networking and once you login, will automatically shutdown again and reboot back into normal mode. Once it is booted into regular mode, the ransomware will execute and begin the encryption process of the victim's computer.
Thanks to Hasherazade's analysis of the ransomware, it was discovered that Cerber uses a JSON configuration file for its settings when executed. This config file details what extensions to encrypt, what countries should not be encrypted, what files and folders to not encrypt, and various other configuration information.
When encrypting your data, Cerber will scan the victim's drive letters for any files that match certain file extensions. When it finds a matching data file, it will encrypt the file using AES-256 encryption, encrypt the file's name, and then add the .CERBER extension to it. As an example, the unencrypted file called test.doc may be renamed as Zu0ITC4HoQ.cerber after it has been encrypted. The currently targeted file extensions are:
Code:
.contact, .dbx, .doc, .docx, .jnt, .jpg, .mapimail, .msg, .oab, .ods, .pdf, .pps, .ppsm, .ppt, .pptm, .prf, .pst, .rar, .rtf, .txt, .wab, .xls, .xlsx, .xml, .zip, .1cd, .3ds, .3g2, .3gp, .7z, .7zip, .accdb, .aoi, .asf, .asp, .aspx, .asx, .avi, .bak, .cer, .cfg, .class, .config, .css, .csv, .db, .dds, .dwg, .dxf, .flf, .flv, .html, .idx, .js, .key, .kwm, .laccdb, .ldf, .lit, .m3u, .mbx, .md, .mdf, .mid, .mlb, .mov, .mp3, .mp4, .mpg, .obj, .odt, .pages, .php, .psd, .pwm, .rm, .safe, .sav, .save, .sql, .srt, .swf, .thm, .vob, .wav, .wma, .wmv, .xlsb, .3dm, .aac, .ai, .arw, .c, .cdr, .cls, .cpi, .cpp, .cs, .db3, .docm, .dot, .dotm, .dotx, .drw, .dxb, .eps, .fla, .flac, .fxg, .java, .m, .m4v, .max, .mdb, .pcd, .pct, .pl, .potm, .potx, .ppam, .ppsm, .ppsx, .pptm, .ps, .pspimage, .r3d, .rw2, .sldm, .sldx, .svg, .tga, .wps, .xla, .xlam, .xlm, .xlr, .xlsm, .xlt, .xltm, .xltx, .xlw, .act, .adp, .al, .bkp, .blend, .cdf, .cdx, .cgm, .cr2, .crt, .dac, .dbf, .dcr, .ddd, .design, .dtd, .fdb, .fff, .fpx, .h, .iif, .indd, .jpeg, .mos, .nd, .nsd, .nsf, .nsg, .nsh, .odc, .odp, .oil, .pas, .pat, .pef, .pfx, .ptx, .qbb, .qbm, .sas7bdat, .say, .st4, .st6, .stc, .sxc, .sxw, .tlg, .wad, .xlk, .aiff, .bin, .bmp, .cmt, .dat, .dit, .edb, .flvv, .gif, .groups, .hdd, .hpp, .log, .m2ts, .m4p, .mkv, .mpeg, .ndf, .nvram, .ogg, .ost, .pab, .pdb, .pif, .png, .qed, .qcow, .qcow2, .rvt, .st7, .stm, .vbox, .vdi, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .3fr, .3pr, .ab4, .accde, .accdr, .accdt, .ach, .acr, .adb, .ads, .agdl, .ait, .apj, .asm, .awg, .back, .backup, .backupdb, .bank, .bay, .bdb, .bgt, .bik, .bpw, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .ce1, .ce2, .cib, .craw, .crw, .csh, .csl, .db_journal, .dc2, .dcs, .ddoc, .ddrw, .der, .des, .dgc, .djvu, .dng, .drf, .dxg, .eml, .erbsql, .erf, .exf, .ffd, .fh, .fhd, .gray, .grey, .gry, .hbk, .ibank, .ibd, .ibz, .iiq, .incpas, .jpe, .kc2, .kdbx, .kdc, .kpdx, .lua, .mdc, .mef, .mfw, .mmw, .mny, .moneywell, .mrw, .myd, .ndd, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nwb, .nx2, .nxl, .nyf, .odb, .odf, .odg, .odm, .orf, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pdd, .pem, .plus_muhd, .plc, .pot, .pptx, .psafe3, .py, .qba, .qbr, .qbw, .qbx, .qby, .raf, .rat, .raw, .rdb, .rwl, .rwz, .s3db, .sd0, .sda, .sdf, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srw, .st5, .st8, .std, .sti, .stw, .stx, .sxd, .sxg, .sxi, .sxm, .tex, .wallet, .wb2, .wpd, .x11, .x3f, .xis, .ycbcra, .yuv
When searching for files to encrypt, Cerber will skip files that are named bootsect.bak, iconcache.db, thumbs.db, or wallet.dat or whose full pathname include the following strings:
Code:
:\$recycle.bin\
:\$windows.~bt\
:\boot\
:\drivers\
:\program files\
:\program files (x86)\
:\programdata\
:\users\all users\
:\windows\
\appdata\local\
\appdata\locallow\
\appdata
oaming\
\public\music\sample music\
\public\pictures\sample pictures\
\public\videos\sample videos\
\tor browser\
Furthermore, Cerber contains the ability to scan for and enumerate unmapped Windows shares and encrypt any data that is found on them. If the network setting is set to 1 in the configuration file, then Cerber will search for and encrypt any accessible network shares on your network, even if those shares are not mapped to the computer.
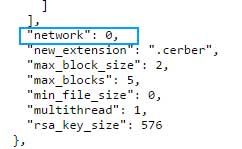
At this time, though this feature appears to be turned off in the configuration file, It is important for all system administrators to harden the security of their network shares as this feature is starting to become common in newer ransomware.
Last, but not least, Cerber will create 3 ransom notes on your desktop as well as in every folder that is encrypted. These files are called # DECRYPT MY FILES #.html, # DECRYPT MY FILES #.txt, and # DECRYPT MY FILES #.vbs.These ransom notes contain instructions on what has happened to your data and contain links to the Tor decryption service where you can make the ransom payment and retrieve the decryptor.
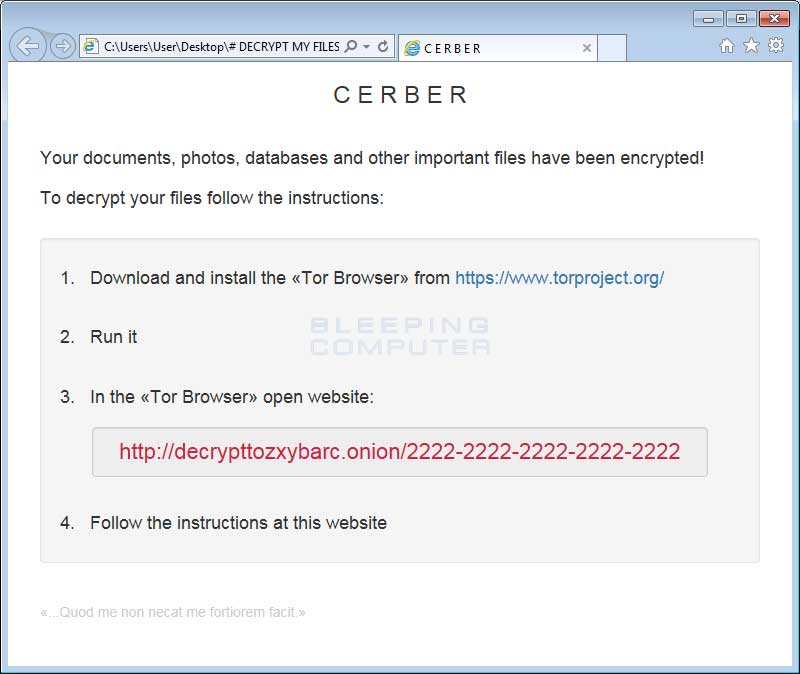
At the bottom of each ransom note contains the Latin quote:
.
Quod me non necat me fortiorem facit
- Cerber Ransom Note
- Cerber Ransom Note
In English, this translates to "That which does not kill me makes me stronger",which I am sure all of the victims appreciate.
B. Cerber Bisa Ngomong Loh
Once of the ransom notes that Cerber creates is a bit more "special" then the others. The # DECRYPT MY FILES #.vbs file contains VBScript, which will cause the victim's computer to speak to them. (jadi muncul suara gitu gan ngasih tau kalo kompi kita udah dienkripsi. silahkan dunlud suaranya disini : http://www.bleepstatic.com/audio/cerber/cerber.mp3 aman kug)
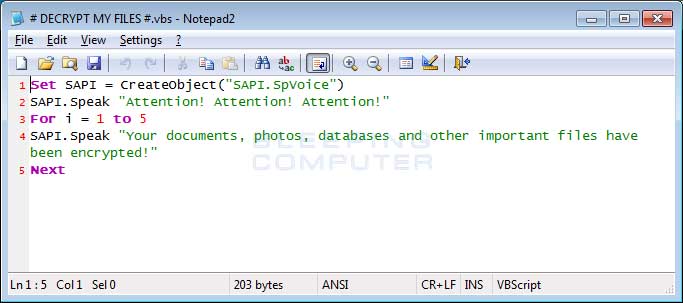
[B]C. KHUSUS PENCEGAHAN AGAR KOMPUTER YANG SEHAT TIDAK TERKENA VIRUS RANSOMWARE.
Disini proteksi nya ada 2 lapis.
Lapis Pertama :
Install Malwarebytes Anti-Ransomware Beta


PERLU DIPAHAMI, MALWAREBYTES ANTI RANSOMWARE INI MASIH BETA, BIASANYA BUG YG MUNCUL CUMAN FALSE POSITIF. SILAHKAN DIGUNAKAN DENGAN MENANGGUNG SENDIRI EFEK SAMPINGNYA, DO WITH YOUR OWN RISK.
LINK DUNLUD : https://malwarebytes.box.com/s/znlaj...4enkik7lreqxd9
VERSI : BETA 8, v.0.9.17.661dirilis tgl 7 September 2016.
Change Log :
Improvements:
Further fine-tuned behavioral detection techniques
Main GUI now closes to the tray instead of only minimizing to the taskbar
Added support to allow exclusion of folders in addition to individual files
Performance improvements to prevent high CPU and memory usage
Further enhancements to prevent false positives
Numerous enhancements to harden the product against malicious tampering attempts
Added basic command line functions for Business version to allow ability to start or stop protection, add or remove exclusions and restore an item from quarantine
Created an MSI version of the Malwarebytes Anti-Ransomware installer for Business version (coming soon...)
Improved side-by-side usage with other Business versions of Malwarebytes products: Malwarebytes Anti-Malware v. 1.x and Malwarebytes Anti-Exploit v. 1.x
Issues Fixed:
Fixed a crash that could occur after a detection and required reboot
Fixed issue where deselecting rows in Quarantine did not work properly
Fixed issue where Dashboard showed mismatched protection state, e.g. showed as disabled even though it was properly enabled and active
Fixed issue where a detection alert would display with no detail populated
Lapis Kedua :
Install CryptoPrevent
Penjelasan apa itu CryptoPrevent+link download CryptoPrevent versi terbaru silahkan menuju ke sini : http://www.foolishit.com/vb6-project...ryptoprevent/#
Penampakan CryptoPrevent versi 7.1 di kompi ane. kalo CryptoPrevent sukses,maka ketika menekan tombol test,muncul notif,prevention success.


INDEX TAMBAHAN
1. VIRUS RANSOMWARE LAMA TAHUN 2015
2. VIRUS RANSOMWARE LAMA TAHuN 2014
3. Komeng dari Kaskuser+Mastah
4. Laporan dari para korban virus Ransomware yang Telah SUKSES mendecrypt/menormalkan file di kompi nya dgn menggunakan tool khusus
5. LANJUTAN DAFTAR KORBAN VIRUS RANSOMWARE

6. Laporan Donasi via paypai
7. Berita Update Terbaru
SEKIAN
gimana gan ? udah panas kepalanya ?

Gak pa pa panas kepalanya gan gara2 baca trit ane,daripada ntar kepala agan dan sista panas gara2 kompinya kena nih virus

Insya Allah ane akan selalu update perkembangan virus ini di trit ini,so jangan lupa subscribe yak

Jika berkenan,bagi
 donk
donk 
tapi ane nolak


Diubah oleh Comdark.Bubnix 18-09-2016 09:16
4iinch dan anasabila memberi reputasi
3
525.5K
4.7K
Komentar yang asik ya
Urutan
Terbaru
Terlama
Komentar yang asik ya
Komunitas Pilihan